The scam formerly known as UICEX and CRGLOBAL is still running, despite countless warnings.
They’ve rebranded yet again — this time as Signal Raiders, using a fresh domain: signalraiders.com.
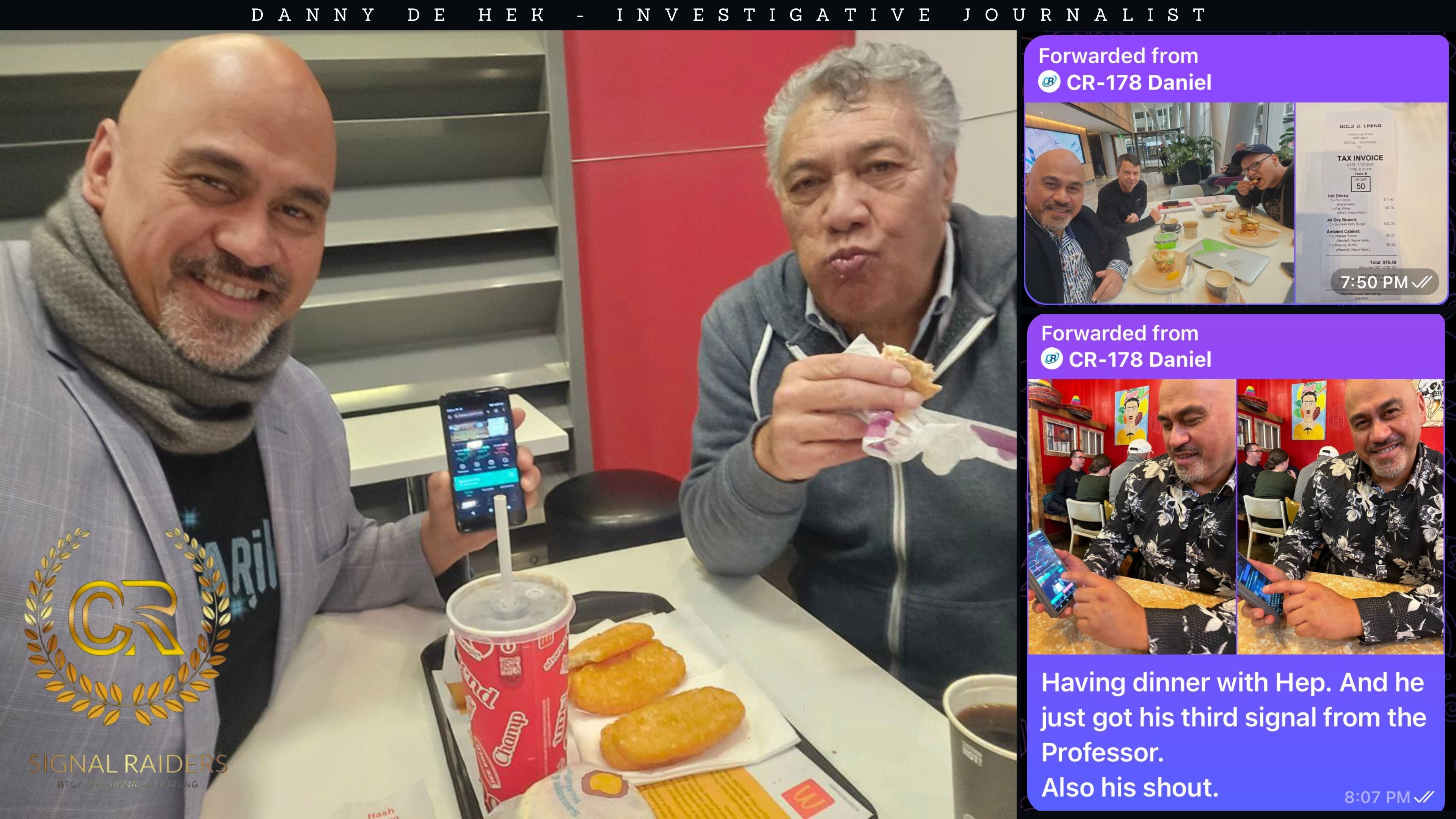
With shiny new graphics and big promises of a “99.6% success rate,” this is just another multi-level crypto trading Ponzi scheme in disguise. This time, it’s being heavily promoted by Hohepa Patea, based in Maungaraki Lower Hutt, Wellington 5010, who openly claims to have quit his job to push this full-time.
But here’s the good news: one of our Avengers got a victim out – and in doing so, uncovered some of the psychological games these scammers use to keep people trapped.
Let’s break it down.
The Original Scam: UICEX / CRGLOBAL
This is the same team that operated under UICEX.com, CR Wealth, and CR Investment Group, running BonChat Telegram groups, fake binary trading signals, and staged Zoom calls to lure in everyday investors.
Key red flags from UICEX included:
- Guaranteed returns on crypto signals
- Rigged “order code” trading using copy-paste instructions (not real trading)
- MLM-style rank bonuses and commissions up to 9 levels deep
- Fake certificates from British Columbia and Colorado (we’ll get to that)
- Surveillance-style tools: using BonChat to monitor members, block screenshots, and block users from withdrawing unless they gave a “reason”
Their aggressive pressure tactics, including minimum $1,000 USDT deposits and false claims of Financial Markets Authority (FMA) approval, caught the attention of multiple watchdogs — but the scam kept morphing.
Now they’re back with a new website and slightly upgraded branding.
Relevant FMA Warning:
In fact, the FMA (Financial Markets Authority) has recently published an updated warning about WhatsApp-based investment scams that mirror Signal Raiders exactly. The advisory, last updated 29 August 2025, describes:
- Fake trading “mentors” in Telegram/WhatsApp groups
- Reward-based recruitment of friends and family
- Promises of guaranteed returns via “trading signals”
- Remote access apps that steal victims’ personal and financial data
- Leaderboards and bonus “prizes” used as bait
- And a familiar cast of characters: the “Professor,” “Coach,” or “Advisor”
The FMA warns that these scams are linked to pyramid selling and remote-access spyware, and urges the public to report any such activity. That’s exactly what we’re seeing here.
The New Rebrand: Signal Raiders

- signalraiders.com (removed by the Avengers on 25 October 2025)
- admin@signalraiders.com
- BonChat ID ANZ99 (used to onboard new victims)
The new homepage promises:
- “Receive BTC/USDT signals with a 99.6% success rate”
- “Risk-Free Trades 100% guaranteed by CR Investments Group”
- “Trade with $100–$5,000. Deposit $300+ to unlock bonus trading capital.”
They promote twice-daily trades on UICEX with “up to 5 phases per signal,” and instruct people t
o paste order codes into their app to “follow signals.”
Nothing has changed — it’s still the same fake trading setup, designed to look like activity while they collect deposits.
Psychological Manipulation & Victim Control
Here’s where it gets dark.
We now have screenshots from a real victim who tried to leave the platform. What happened next was textbook scam psychology:
“You are one of our family. Please don’t make a decision you will regret. Just withdraw some — not all — and tell others it was your own choice. Help us continue the project.”
They begged the victim not to withdraw all their funds, implying they’d only be allowed to leave if they left money behind.
They even fabricated a “reason” for withdrawal the victim had to submit — such as “I’m renovating a house” — to be approved. Victims who didn’t provide a reason or tried to speak out were muted or removed from BonChat.
This cult-like emotional manipulation is key to how they retain members:
- Guilt-tripping: “Don’t betray the group”
- Gaslighting: “The haters just don’t understand our vision”
- False scarcity: “We’re launching soon — that will prove all the doubters wrong”
- Reputation management: “Say you chose to leave, not that the platform failed”
If this reminds you of Hyperverse, Validus, or any of the major MLM scams — that’s because it’s the same playbook.
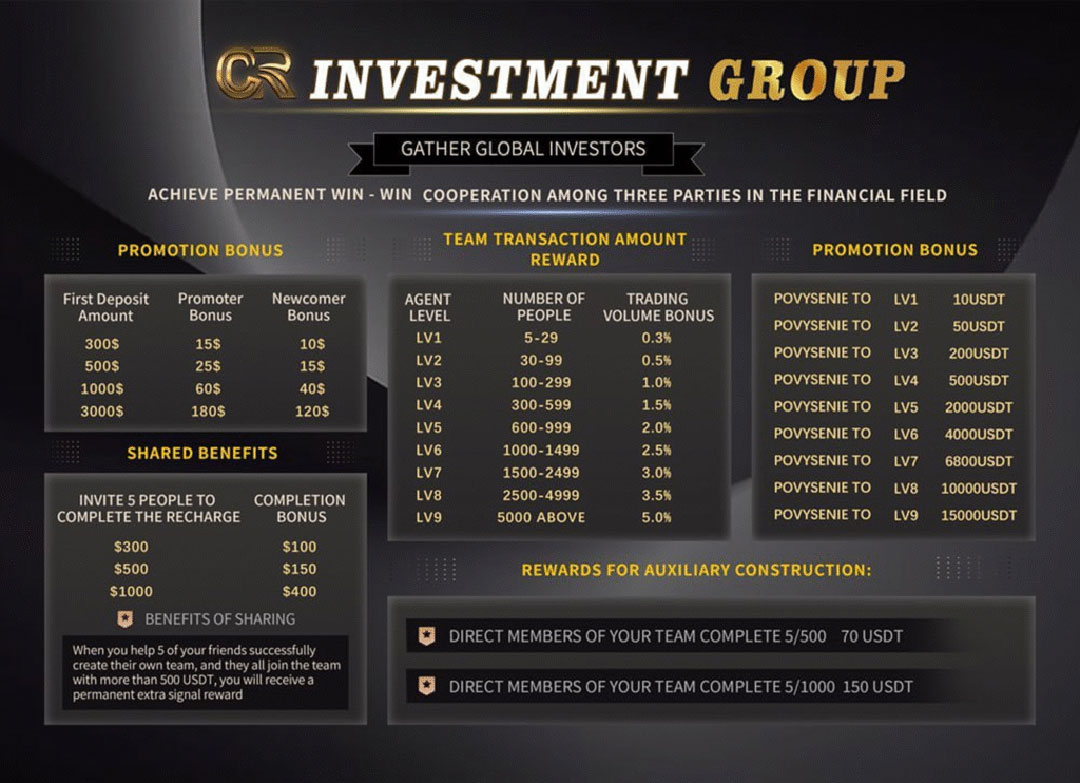
MLM Compensation Plan = Obvious Ponzi Structure
Let’s be very clear: this is a multi-level crypto scam using a “signals” story as the product front.
Here’s what they promise:
- Team commissions from Level 1 to Level 9
- Bonuses for bringing in new people
- Extra signal rewards if your referrals invest more than $500 USDT
- Fake “promotion rewards” up to 150,000 USDT
- “Completion bonuses” for getting 5 people to fund accounts
This is a textbook MLM Ponzi setup, with all the signs:
- Incentivising constant recruitment
- “Team construction” = fake network growth
- Fixed deposits = no real investment activity
- “Risk-free signals” = no real trading strategy
Fake Incorporation Documents
To look legitimate, the scammers show off flashy certificates.
- A British Columbia registration (dated March 20, 2025) for UIC Exchange Limited
- A Colorado share certificate showing 50 million shares issued to “Taylor Fox” — a name that appears nowhere else
But these registrations mean nothing. Anyone can register a business in BC or Colorado — it doesn’t mean they’re licensed to handle financial products or run a crypto exchange.
This is a common MLM scam tactic: register a shell company, then parade the paperwork to appear trustworthy.
Victim Surveillance via BonChat
The BonChat group plays a central role in controlling participants:
- You must join via referral ID (e.g. ANZ99)
- They block screenshots of messages
- They pressure users to post “thank-you” videos if they receive a withdrawal or prize
- If you say anything negative, you’re banned or muted
They offer fake prize draws (microwaves, lunch vouchers, 30 USDT) to keep people engaged — but only if they keep investing or bringing others in.
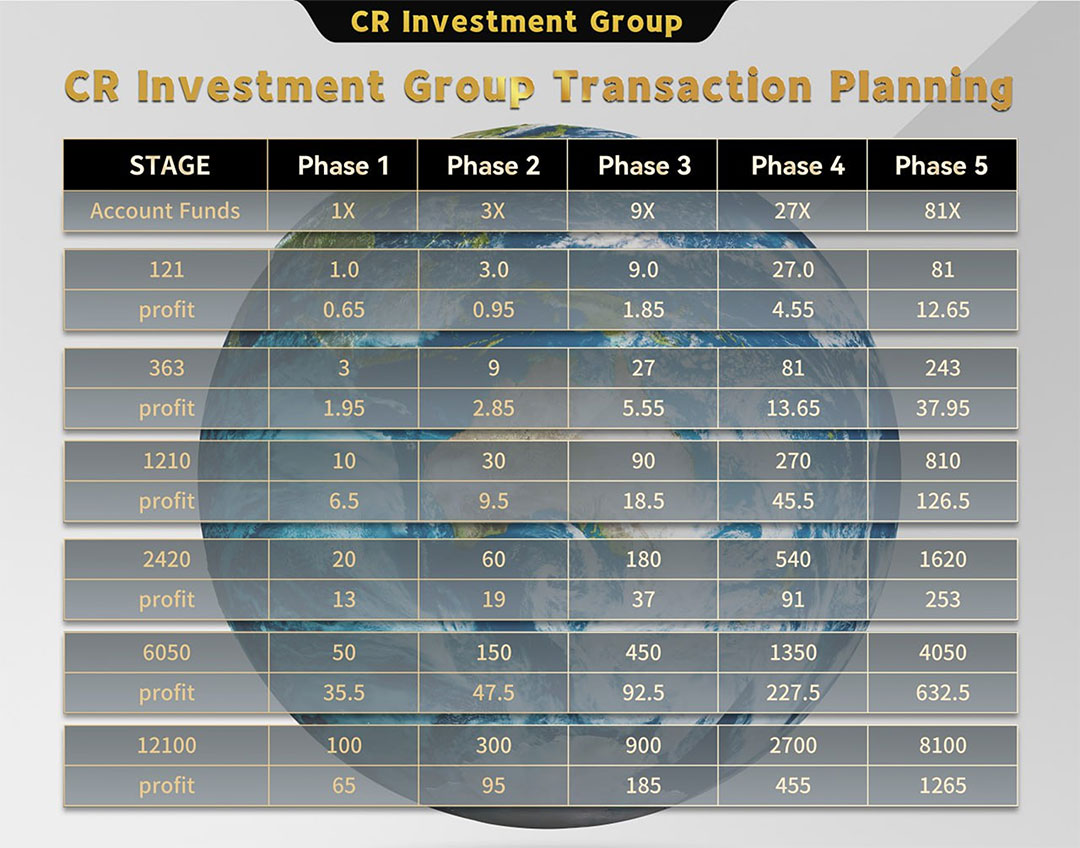
The Exit Trap: Rewards, Reinvestment, and False Hope
Their staged presentations show:
- “Transaction Planning” with 81X returns
- Payouts listed in multiple “phases” that require reinvestment
- Pressure to “only withdraw partial profits”
It’s designed so you never fully withdraw your principal. You’re always cycling into the next phase — until the rug is pulled.
The Escape: One Victim Gets Out
This time, one of our trusted Avengers helped a victim escape. After carefully guiding them through the withdrawal process (including creating a fake reason for leaving), the victim was finally able to get most of their funds out.
They left a small balance behind — a necessary “peace offering” to exit the platform.
This is a rare success story — and a reminder that community resistance works.
We’ve now documented:
- The latest domain: signalraiders.com
- The BonChat invitation method
- The fake incorporation trail
- The full MLM commission structure
- And the emotional control tactics they use
Stay Vigilant – They’ll Rebrand Again
These scammers switch domains, rename their groups, and pretend it’s a “new project” every time the heat rises.
We’ve seen this same team cycle through:
- UICEX
- CRGLOBAL
- CR Wealth
- Signal Raiders
… and more will follow.
We’re tracking their digital footprint, exposing their lies, and helping victims escape when we can.
If you were targeted, manipulated, or pressured to deposit — you’re not alone. Contact us via dehek.com/contact and we’ll help you document what happened.
Name the scam.
Expose the team.
Warn the next victim.
Flagged Domains Previously Used in This Scam
The Financial Markets Authority (FMA) in New Zealand has identified and listed hundreds of domain names previously used to promote this ongoing investment scam. While most of these domains have since been shut down, new ones are created regularly as part of an aggressive effort to stay ahead of regulators and continue defrauding unsuspecting investors.
This is not a one-off scam — it’s an industrial-scale operation using throwaway domains, offshore registration, and fake trading platforms. Below is a non-exhaustive list of websites that have been associated with this criminal network. If you recognise any of these, do not engage, and warn others:
133exchange.com, 68ea-idn.com, 68ea-mys.com, 68ea-us.com, 68ea.app, 68ea.com, 68ea02.com, 68ea1.com, 68ea2.com, 68ea3.com, 68eamys.com, 68eaus.com, 888okx.com, admin.bexvip.cc, admin.btpex.cc, admin.btpex.net, agent.bexus.cc, agent.btpex.cc, agent.btpex.net, api.bexus.cc, api.bexvip.cc, api.btpex.cc, api.btpex.net, bcbex.cc, bexus.cc, bexvip.cc, btpex.cc, btpex.net, btex12.com, cbex-dex.com, cbex.cx, cbex.lol, cbex18.com, cbex28.com, cbex29.com, cbex3.com, cbex38.com, cbex39.com, cbex53.com, cbex58.com, cbex69.com, cbexe.com, cbexo.com, cbextp.com, crglobal.vip, dbbcce.com, dobibo.com, dobibo.lol, dobibo.me, dobibo.pro, dobibo1.com, dobibo11.com, dobibo12.com, dobibo13.com, dobibo15.com, dobibo16.com, dobibo2.com, dobibo3.com, dobibo31.com, dobibo32.com, dobibo33.com, dobibo35.com, dobibo36.com, dobibo5.com, dobibo51.com, dobibo52.com, dobibo53.com, dobibo55.com, dobibo56.com, dobibo6.com, dobiboak.com, dobibop.com, dobibopk.com, dobibopp.com, dobibops.com, dobibopx.com, dsj10.com, dsj15.com, dsj33.com, dsj8.com, dsj96.com, dsj99.com, dsjads.com, dsjex.net, dsjex.pro, dsjex.shop, dsjex.xyz, dsjex112.com, dsjex321.com, dsjex369.com, dsjex66.site, dsjex789.com, dsjex88.blog, dsjex998.com, dsjoo.com, dsjqq.com, dsjvv.com, frtaaa.com, frtam.com, frtap.com, frtau.com, frtfl.com, frtee.lol, frtecc.com, frtexc.com, frtexch.com, frtmn.com, frtsss.com, frtvip.com, frtvvip.com, grok-zen.com, grokr-lss.com, grokr-lssc.com, grokr6688.com, grokr88.com, grokrapp66.com, grokrbbio.com, grokrbeef.com, grokrc.com, grokrc66.com, grokrc9idd.com, grokrccce.com, grokrcd.com, grokrckdd8.com, grokrcllde.com, grokrco.com, grokrcoin.com, grokrd.com, grokrdisei.com, grokrex88.com, grokrexcci.com, grokrexddu.com, grokrexkk.com, grokrexooc.com, grokrexssci.com, grokrforcc.com, grokrhot3.com, grokrai5rt.com, grokraicdo6.com, grokraichc.com, grokraidee.com, grokraiss.com, grokrook6.com, grokrsa.com, grokrse.com, grokrsoll.com, grokrsx.com, grokrwaid.com, growsub.com, hellobit-app.com, hellobit1.com, hellobit11.com, hellobit12.com, hellobit13.com, hellobit15.com, hellobit2.com, hellobit3.com, hellobitb.com, hellobitc.com, hellobitd.com, hellobitg.com, hellobitk.com, hellobito.com, hellobitpro.com, hellobitq.com, hellobitx.com, hellobilg.com, hellobilx.com, hhhe.bar, hhhe.fyi, hhhe.icu, hhhe.in, hhhe.lol, hhhe.pw, hhhe.tv, hhhe1.com, hhheap.com, hhhees.com, hhheev.com, hhheex.com, hhhetp.com, hhheux.com, hhhewp.com, hhhexp.com, hhheyy.com, hhtxex.com, ijex.bet, ijex.com, ijex.pro, ijex15.com, ijex35.com, ijex38.com, ijex51.com, ijex53.com, ijex55.com, ijex56.com, ijex63.com, ijex9.com, ijexcp.com, ijexdk.com, ijexp.com, ijexpa.com, ijexpe.com, ijexpv.com, ijexpy.com, ijexqa.com, ijexqp.com, ijexw.com, ijexzp.com, lbank-t666.com, lkycd.com, lkyaa.com, lkyexch.com, lkyjud.com, lkyjyj.com, lkyoo.com, lkyrr.com, lkyus.com, lkyve.com, lkyvpp.com, lkytwt.com, lvgtur.com, lw-ex.com, lwex.app, lwex.com, lwex.ltd, lwex00.com, lwex01.com, lwex01.org, lwex02.com, lwex02.org, lwex03.com, lwex03.org, lwex04.com, lwex05.com, lwex05.org, lwex1.org, lwex2.org, lwex3.com, lwex3.org, lwex4.com, lwex5.org, lwexapp.com, lwexlt.com, lwex-sk.com, lwexsk.com, okoexchange.com, okoexit.com, okoexin.com, okoexpro.com, pnenot.com, sdgsgo.com, siuek.com, uwcmbe.com, mantistrade.com, optcoin.com, optcoin.lol, optcoin.pro, optcoin1.com, optcoin12.com, optcoin13.com, optcoin15.com, optcoin2.com, optcoin21.com, optcoin22.com, optcoin23.com, optcoin25.com, optcoin36.com, optcoin4.com, optcoin5.com, optcoin51.com, optcoin53.com, optcoin54.com, optcoin55.com, optcoin56.com, optcoin61.com, optcoin63.com, optcoin64.com, optcoin65.com, optcoin8.com, optcoin9.com, optcoinap.com, optcoinoe.com, optcoinwk.com, optcoinwp.com, pcex.bet, pcex.com, pcex.fun, pcex.one, pcex.org, pcex.pro, pcex.xyz, pcex11.com, pcex12.com, pcex19.com, pcex21.com, pcex23.com, pcex28.com, pcex29.com, pcexak.com, pcexapa.com, pcexapa.net, pcexdk.com, pcexkk.com, pcexpk.com, pcexpv.com, pcexpy.com, pcexq.com, pcexqp.com, pcexwk.com, rayxe.com, rayqme.com, raycfy.com, rayxdt.com, rayvgu.com, rayzsr.com, rayht.com, rayxxc.com, rayjjl.com, raybmn.com, rayffy.com, rayccx.com, rayuuv.com, rayhht.com, rayool.com, rayqww.com, rayttp.com
UPDATE: Legal Threat Issued by Andrew Davis of Treadwells Law

For transparency, the full letter can be viewed here: [PDF: Letter from Andrew Davis]
The letter contains several factual inaccuracies about my work and makes a number of claims that are easily disproven by verifiable evidence.
One statement in particular must be addressed directly. Mr Davis wrote:
“Furthermore, you have mocked and mispronounced Mr Patea’s Māori name in a way which is unquestionably racially offensive and disrespectful.”
This allegation is completely unfounded.
As someone with dyslexia, occasional mispronunciation is a well-documented neurological difficulty — not an act of racism, malice, or disrespect.
There is no legal or ethical requirement in New Zealand for journalists to pronounce names perfectly, and the accusation trivialises genuine issues of racism by weaponising a disability as a rhetorical tool.
For clarity:
- I do not have a Facebook account, despite Mr Davis alleging I posted there.
- No podcast episode exists on this subject, despite his suggestion otherwise.
- The investigation is based entirely on open-source intelligence, recorded material, and first-hand victim evidence.
What the letter does not address is far more telling:
- It does not dispute the factual accuracy of the FMA’s official scam warning.
- It does not challenge any of the documented evidence of recruitment pressure, withdrawal issues, or deceptive behaviour.
- It does not provide any explanation for why Mr Patea is promoting a scheme that matches exactly the scam profile described by the FMA.
Here again is the relevant FMA warning, which outlines the same operation Mr Patea is promoting:
FMA Warning – “TXEX / WhatsApp Educational & Investment Platform Scam”
https://www.fma.govt.nz/library/warnings-and-alerts/txex/
Right of Reply Given — Before Any Publication
On 25 October 2025, before publishing anything, I contacted Hohepa Patea directly via text — at the time, he had no publicly available business contact details.
I offered him a full right of reply and invited him to respond to:
- the FMA warnings
- the legitimacy of the platform
- withdrawal barriers
- recruitment incentives
- victim testimony
He did not respond.
His only reply came later, through the lawyer’s letter attached above.
New Evidence Since the Legal Threat
Following the letter, additional material emerged from victims and whistleblowers, including:
- screenshots of Mr Patea actively promoting CRGLOBAL/UICEX/Signal Raiders,
- messages showing pressure placed on recruits,
- and confirmation from a victim who invested $2,500, whom we successfully assisted in withdrawing funds before further loss.
This evidence aligns precisely with the behaviours described in the FMA’s scam warning.
Transparency and Public Record

- The original lawyer’s letter is attached above.
- My full written reply, including additional screenshots demonstrating Mr Patea’s involvement, is available here: [PDF: Danny’s Reply Letter]
This investigation will continue as further evidence is reviewed.
Disclaimer: How This Investigation Was Conducted
This investigation relies entirely on OSINT — Open Source Intelligence — meaning every claim made here is based on publicly available records, archived web pages, corporate filings, domain data, social media activity, and open blockchain transactions. No private data, hacking, or unlawful access methods were used. OSINT is a powerful and ethical tool for exposing scams without violating privacy laws or overstepping legal boundaries.
About the Author
I’m DANNY DE HEK, a New Zealand–based YouTuber, investigative journalist, and OSINT researcher. I name and shame individuals promoting or marketing fraudulent schemes through my YOUTUBE CHANNEL. Every video I produce exposes the people behind scams, Ponzi schemes, and MLM frauds — holding them accountable in public.
My PODCAST is an extension of that work. It’s distributed across 18 major platforms — including Apple Podcasts, Spotify, Amazon Music, YouTube, and iHeartRadio — so when scammers try to hide, my content follows them everywhere. If you prefer listening to my investigations instead of watching, you’ll find them on every major podcast service.
You can BOOK ME for private consultations or SPEAKING ENGAGEMENTS, where I share first-hand experience from years of exposing large-scale fraud and helping victims recover.
“Stop losing your future to financial parasites. Subscribe. Expose. Protect.”
My work exposing crypto fraud has been featured in:
- Bloomberg Documentary (2025): A 20-minute exposé on Ponzi schemes and crypto card fraud
- News.com.au (2025): Profiled as one of the leading scam-busters in Australasia
- OpIndia (2025): Cited for uncovering Pakistani software houses linked to drug trafficking, visa scams, and global financial fraud
- The Press / Stuff.co.nz (2023): Successfully defeated $3.85M gag lawsuit; court ruled it was a vexatious attempt to silence whistleblowing
- The Guardian Australia (2023): National warning on crypto MLMs affecting Aussie families
- ABC News Australia (2023): Investigation into Blockchain Global and its collapse
- The New York Times (2022): A full two-page feature on dismantling HyperVerse and its global network
- Radio New Zealand (2022): “The Kiwi YouTuber Taking Down Crypto Scammers From His Christchurch Home”
- Otago Daily Times (2022): A profile on my investigative work and the impact of crypto fraud in New Zealand








Leave A Comment